If you searched barapk org, you’re likely after quick access to Android apps without drama. This guide shows how to get the convenience you want while protecting your phone, data, and wallet—by favoring safe APK downloads, understanding Android sideloading, practicing strict permissions hygiene, and choosing services that respect copyright compliance and developer rights. You’ll learn how to verify files, sandbox unknown apps, keep updates clean, and spot red flags in seconds so your device stays fast, private, and malware-free.
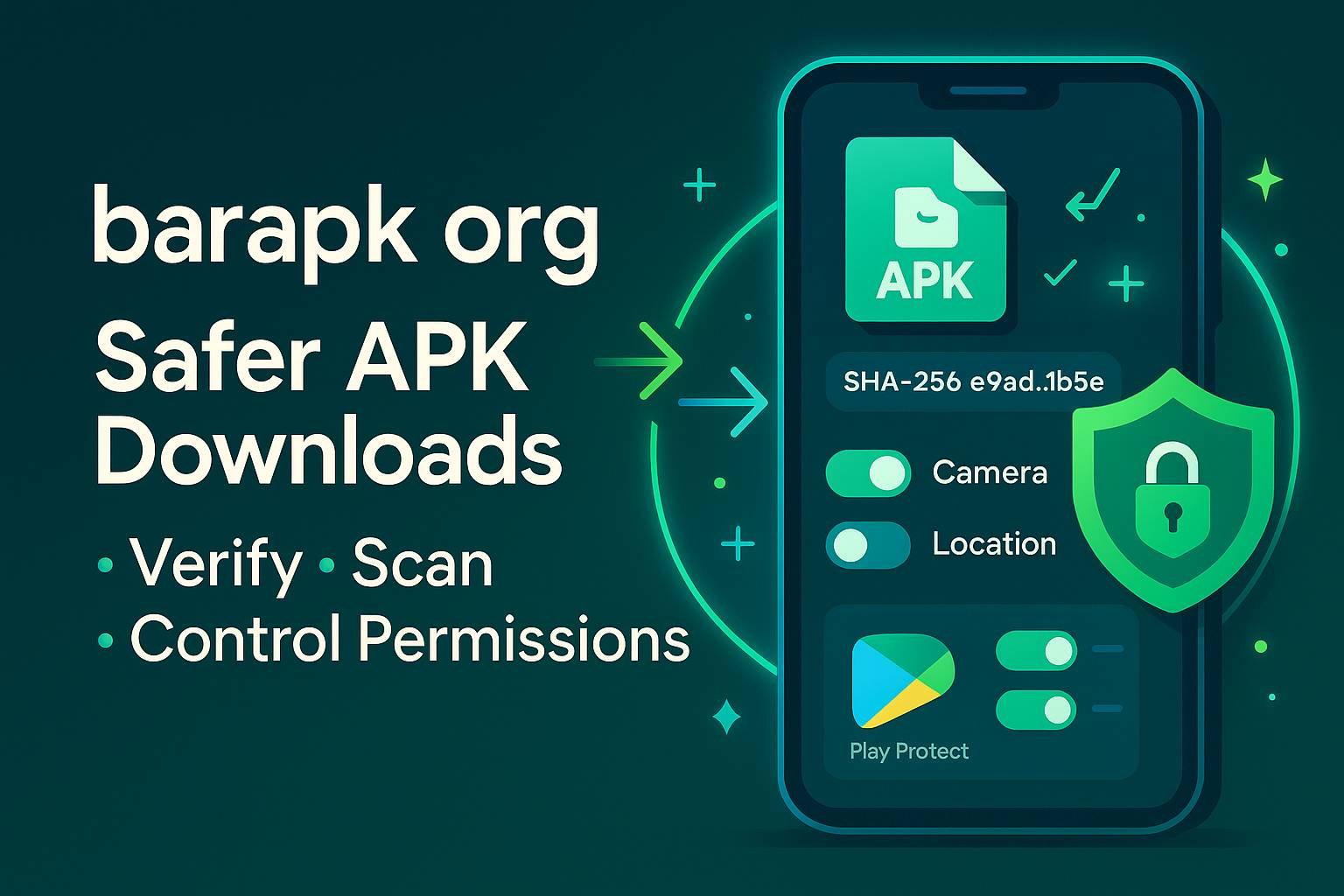
An APK is simply an Android app package. Google Play and other vetted stores add trust layers: scanning, policy enforcement, and an easy update strategy. Sideloading means installing from outside those stores. That can be legitimate (beta builds, enterprise apps, open-source apps)—but only when you pair it with Android app security habits like verifying the developer’s identity, checking the SHA-256 checksum, and scanning with Play Protect or a reputable mobile security tool before you ever tap “Install.”
Treat barapk org like a search phrase that leads you to pages to evaluate—not a built-in trust badge. Any site you visit should pass a quick health check: modern HTTPS, clear ownership, transparent privacy policy, no forced extension installs, and no claims to bypass DRM. If a page promises modded APKs or “premium for free,” that’s your cue to leave; it violates copyright compliance and often hides malware risks behind glossy buttons.
Keep your posture simple: prefer official app stores; when you must sideload, use terms-of-service-compliant sources; and never download paid apps for free. This protects you from lawsuits and from the bigger day-to-day costs—keyloggers, SMS fraud, and data brokerage. Supporting developers through legitimate channels funds updates, fixes, and the very features you’re looking for.
Adopt a habit you can finish in minutes: (1) confirm the app’s real publisher and website; (2) verify the APK signature or listed SHA-256 checksum; (3) scan locally with Play Protect and one reputable scanner; (4) review app permissions before first launch; (5) run it in a sandbox or emulator for thirty seconds to spot odd network calls. Done consistently, this routine eliminates most bad installs.
Look for a normal domain history and clear contact details. Pages should show version history, changelogs, and intact cryptographic signatures (not “re-signed by uploader”). Ads should be ordinary—not forced redirects, fake system pop-ups, or “virus detected” scareware. Good pages avoid “double download” traps and never require you to disable security settings beyond standard install unknown apps toggles per app.
A SHA-256 checksum is a fingerprint; if the number from the site matches the number you compute locally, the file wasn’t altered in transit. The APK signature is stronger: Android checks it at install, but you can also compare the developer’s certificate (issuer/subject, fingerprint) against the one used on Play or on the developer’s official page. Mismatches aren’t “probably fine”—they’re a stop sign.
Grant the minimum. If a photo editor asks for SMS or Contacts on day one, decline and watch whether the app still works. Use Android’s “Allow only while using the app,” “Ask every time,” and toggles like Nearby devices and Background location sparingly. Periodically review privacy dashboard and revoke what’s stale. Tight permissions hygiene is the simplest, strongest defense you control.
Keep a tiny toolkit: a checksum app to verify SHA-256, an open-source firewall to block suspicious traffic, a local network monitor, and a reputable mobile security scanner. Add an emulator on desktop for first-run smoke tests. With these in place, safe APK downloads feel like second nature—quick, deliberate, and low-stress.
Unknown developer? Launch in an emulator. If that’s overkill, install inside a work profile (via Android’s work/managed profile tools) so it gets a separate data container. Watch network calls, CPU bursts, and wake-lock behavior. If an app tries to open accessibility services or ask for device admin without a clear need, uninstall immediately.
Avoid pages pushing modded APKs, “anti-ban builds,” cracked subscriptions, or anything that claims to defeat licensing. Beware “verification” steps that demand surveys or profile logins. Steer clear of installers wrapped in a “downloader” EXE on desktop—classic malware risks. Your device, identity, and bank are worth more than a shortcut.
Prefer official app stores first; when a developer distributes off-store builds, download directly from their verified site or code repository. Explore open-source apps catalogs curated for security and transparency. These ecosystems emphasize reproducible builds, clear license compliance, and privacy-respecting defaults—great for browsers, note apps, readers, and utilities you use daily.
If an install asks for you to sign in, use two-factor authentication on that account, a unique password, and device-bound sign-in where possible. Separate emails for experiments help quarantine risk. Lock down recovery options so a bad actor can’t pivot from one compromised app into your cloud, photos, or banking.
If an app behaves oddly—ads outside the app, phantom notifications, battery spikes—force stop, revoke permissions, uninstall, and run a scan. Change passwords on any account you used with it. Check notification access and device admin lists for lingering hooks. In the worst case, back up essentials and factory reset; it’s the surest way to evict stubborn adware.
Updates are where many shady sites slip in altered builds. Favor sources that publish version history and changelogs with hashes. Set a monthly update strategy: batch-update trusted apps, then hold a week before updating mission-critical ones to let early bugs shake out. On Android, you can stage updates while the old version remains installed—less downtime, fewer surprises.
Unvetted apps can hammer I/O and wake the CPU. Use Settings → Battery/Storage to spot offenders. If a sideloaded app over-indexes logs or cache, it’s a smell. Pair Android app security with performance discipline: uninstall what you don’t use, clear caches periodically, and avoid “optimizers” that kill useful services or inject ads.
For kids’ phones, lock Play installs to age-appropriate content, disable install unknown apps globally, and create a rule: no apps from links. Teach “why permissions matter” by reviewing requests together. If you test APKs as a hobbyist, keep that on your own device or a separate emulator—never mix experiments with a child’s device.
Root expands power and attack surface. Many modded APKs target rooted devices, installing silently or burrowing into system folders. If you do root, isolate banking and identity to an unrooted phone, keep a clean backup image, and expect certain apps to refuse to run. For most people, stock Android with good privacy settings is safer and simpler.
Need a common app? Use an official app store. Need a developer beta? Download from the developer’s verified site and verify SHA-256. Need open tools? Favor open-source apps with public code and reproducible builds. See “mod,” “hack,” or “premium free”? Close tab. Any step asks for your card or ID unexpectedly? Close tab twice.
Minute 1–2: install a checksum tool and enable Play Protect. Minute 3–4: add an open-source firewall and block background data on unknown apps. Minute 5–6: create a work profile for testing. Minute 7–8: write a two-line install checklist (“verify hash → scan → review permissions”). Minute 9–10: purge sketchy download managers and pin your trusted sources.
Set analytics/telemetry to “off” where possible, deny Background location, and trim Notifications to essentials. Use per-app language and photo-picker scopes (Android 13+) to narrow exposure. Good permissions hygiene keeps sensitive data from being siphoned by a single sloppy install.
Automate photo and document backups to a trusted cloud or local NAS. Export app data where apps support it. When you try a new APK, capture a quick system backup or restore point if your device allows it. Knowing you can roll back in five minutes makes experimentation calm instead of risky.
Open, tap around, then lock the phone for a few minutes. If the app keeps the CPU humming or throws notifications while idle, it’s noisy. Next, check Data Usage: big spikes for a simple tool are suspicious. Finally, long-press the app in Settings → App details and scan its requested permissions against its purpose. A flashlight doesn’t need Contacts; a notes app doesn’t need SMS.
Download only when you need to. Delete installers after use. Keep your browser lean (few extensions, tight browser security settings). Run periodic scans, but trust prevention more than cleanup. Above all, resist FOMO: most “exclusive” APKs are the same app wrapped in adware.
Let the phrase barapk org remain a search breadcrumb you evaluate with your five-step habit. If a page genuinely distributes the developer’s unmodified build with a verifiable APK signature and clear SHA-256 checksum, it can be part of a cautious workflow. If not, you already know the safer alternatives—official app stores, developer sites, and curated open-source apps catalogs.
Installer won’t open? Re-download and verify the hash; corrupt files happen. “App not installed”? Conflicting signature—uninstall old build or skip the new one. Endless ads after install? Revoke notification access, uninstall, clear browser cache, and scan. Battery drain? Restrict background, then uninstall if it persists.
Set a 15-minute weekly window to explore new apps. Anything that doesn’t fit waits a week. This keeps you from chasing shiny objects and piling on risky installs. A tiny schedule change does more for Android app security than any antivirus.
The goal isn’t to avoid sideloading forever; it’s to do it deliberately. With safe APK downloads, strict permissions hygiene, and quick verification steps, you get the flexibility of trying new tools while staying inside legal and ethical lines. Over time, you’ll trust your process—and spend more time using great apps instead of cleaning up after bad ones.
Prefer official app stores and verified developer sites; if you sideload, verify SHA-256 and APK signature every time; practice tight permissions hygiene; scan with Play Protect; sandbox first runs in an emulator or work profile; avoid modded APKs and anything that breaks copyright compliance; keep a simple update strategy; and back up before big changes. Do that, and your Android life stays fast, private, and confident—no matter where your search for barapk org leads next.